By default, Windows Firewall with Advanced Security blocks ICMP Echo Requests from the network. If you want to enable like for monitoring uptime purposes, you can follow this step :
Prerequisites
- An administrative access of Windows Server (In this tutorial: I'm using Windows Server 2012 R2 Standard)
Instructions (Global)
This instruction will make your Windows Server pingable from Global access (anyone can ping your windows server).
- Search for
Windows Firewall with Advanced Securityand click to open it. - From the left pane of the resulting window, click Inbound Rules.
- In the right panel, find the rules titled
File and Printer Sharing (Echo Request - ICMPv4-In). - Right-click each rule and choose Enable Rule.
Instructions for Restricted IP addresses
This instruction will make your Windows Server only pingable from the listed IP Addresses.
For example :
I want only UptimeRobot can ping my Windows Server, so i had to create a new Inbound Rules by :
- Click
New Inbound Rule Wizard - Choose Custom (custom rule) on Rule Type, click Next
- Choose All programs on Program Step
- On Protocol and Ports step, choose
ICMPv4on Protocol type and then click Next - On Scope Steps, add the following IP Address to ensure UptimeRobot can ping your Windows Server on
Which remote IP Addresses does this rule apply tosection :
https://uptimerobot.com/help/locations/
and https://uptimerobot.com/inc/files/ips/IPv4.txt
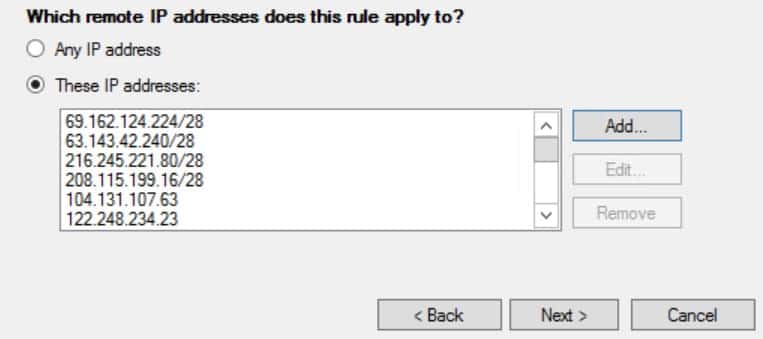
Click Next, choose Action: Allow the connection, and check the Public on Profile step.
Add inbound rules name : Only UptimeRobot can ping
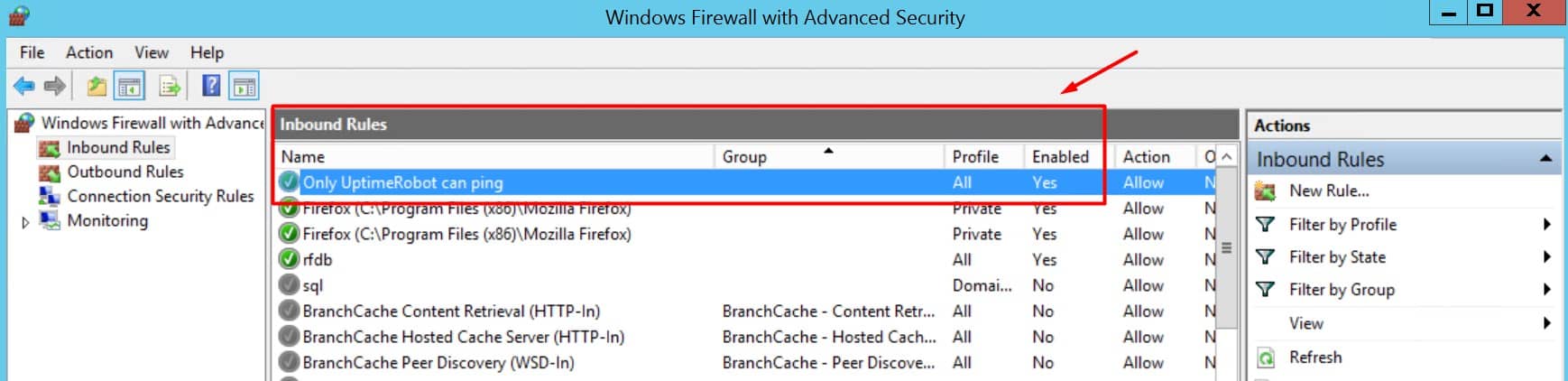
and finally, UptimeRobot can ping my server.
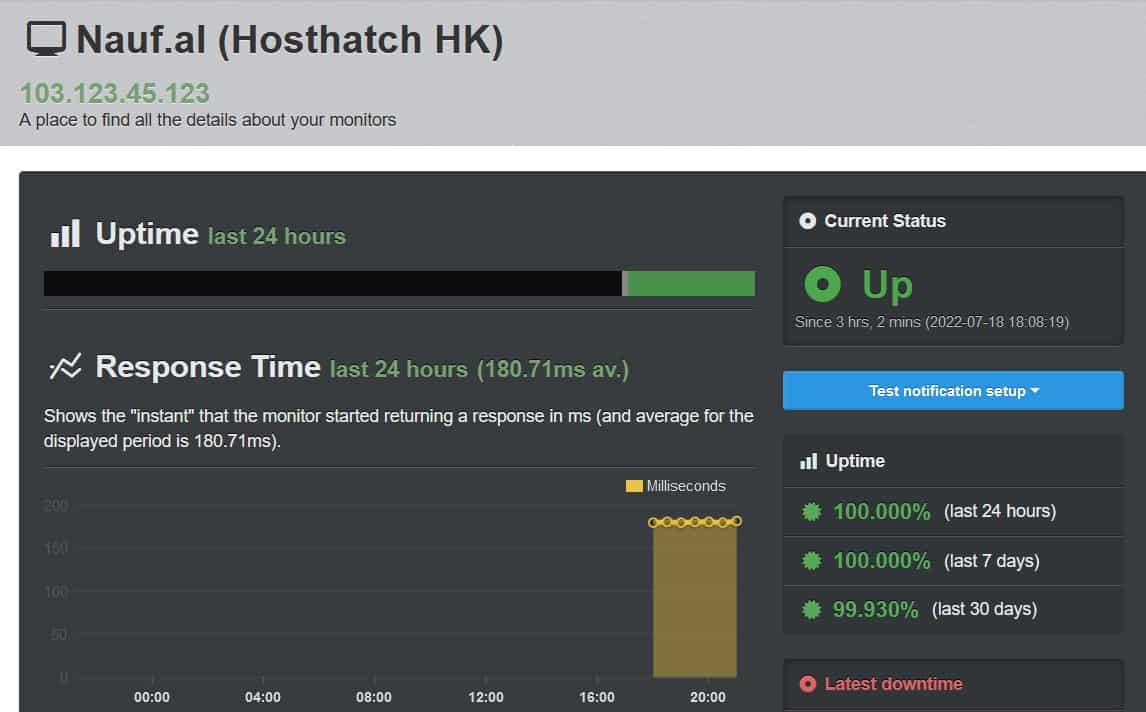
-- update 27/07/2022
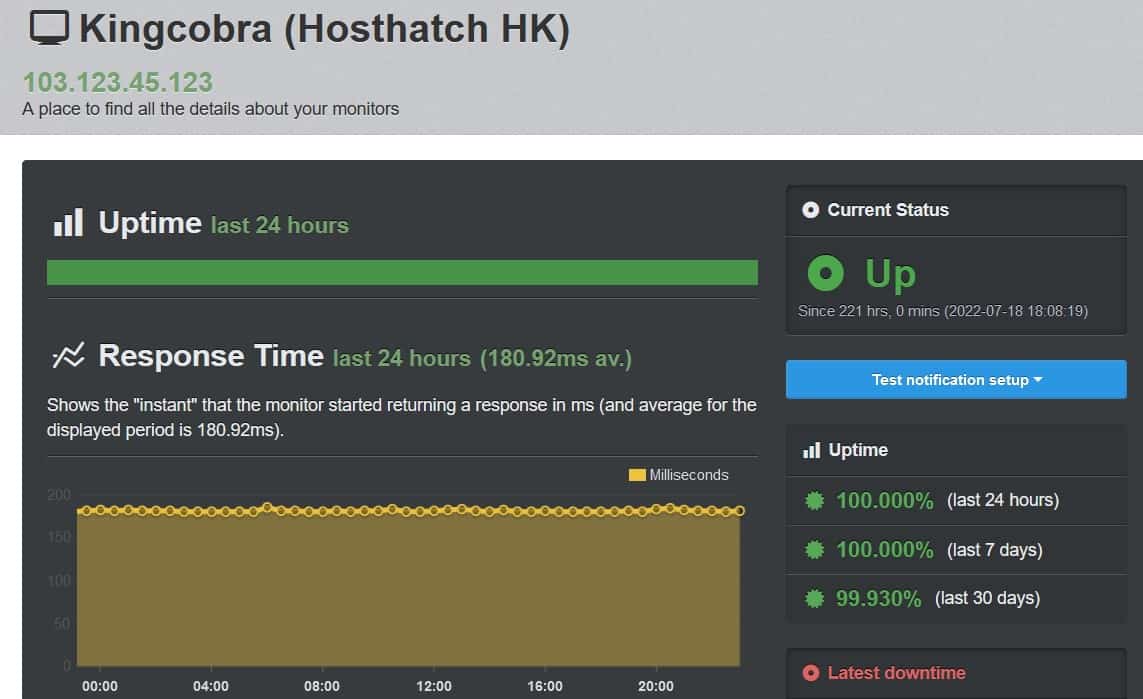
Configure the Windows firewall to allow pings
On this page: