So, I got a task from my client today, they give me a zip with three required files to install an SSL:
- a private key file
privkey.txt - a csr file
filecsr.txt - and a crt file
cert.crt
I want to install the wildcard SSL on NGINX.
The first thing I have to do is extracted the zip to directory /etc/nginx/ssl. Open ssh terminal and use the following command:
mkdir -p /etc/nginx/ssl
unzip wildssl.zip -d /etc/nginx/sslthen move to directory /etc/nginx/ssl by using the following command:
cd /etc/nginx/ssland in order to make the required ssl files (fullchain.pem, and privkey.pem) properly, let me describe with a picture to make it easy to remember:
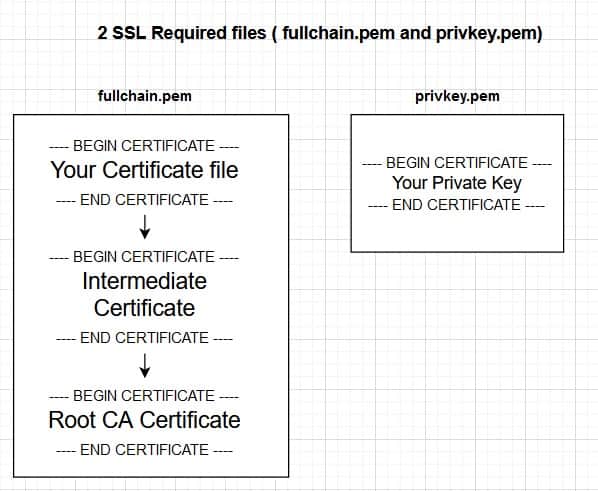
First, I must copy and paste all characters including the —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—– lines from the main certificate file (cert.crt), and then copy Intermediate and Root CA certificates from our SSL Certificates vendor, and combine them into one .pem file.
Open your favorite editor, like maybe nano. I don't comfortable with vim😂
to create a fullchain.pem file
nano fullchain.pemIn this case, I'm using AlphaSSL Wildcard SSL, so I must copy Intermediate Certificate and Root CA with the lines below
New AlphaSSL / Wildcard Intermediate certificate
-----BEGIN CERTIFICATE-----
MIIESzCCAzOgAwIBAgIOSMqBefg+ikLz9c3isT8wDQYJKoZIhvcNAQELBQAwTDEg
MB4GA1UECxMXR2xvYmFsU2lnbiBSb290IENBIC0gUjMxEzARBgNVBAoTCkdsb2Jh
bFNpZ24xEzARBgNVBAMTCkdsb2JhbFNpZ24wHhcNMTYxMDE0MDAwMDAwWhcNMjQw
MjIwMTAwMDAwWjBMMQswCQYDVQQGEwJCRTEZMBcGA1UEChMQR2xvYmFsU2lnbiBu
di1zYTEiMCAGA1UEAxMZQWxwaGFTU0wgQ0EgLSBTSEEyNTYgLSBHMjCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANoB7OTsc2D7fo9qt8YX45JkMtSsANmi
D7nt7muKhsqSZ9l0111HAjyPQNaebRTNw9opOacPBQpoomYaHsSyi3ZY5atdHY9A
szmL7x6DfSLQ46kALuxTz2IZhUQoTMAny3sO7BBkABCkBcygcr5BbDFbSOSx7Lkj
61VN0H1iSqW0paRZhcUlkab+pgmfBhBtj4EMZEBecwCa4C5lmFQQAHCYyOHtNF/Y
nMcNwNYjWUX8/lV6hu6UYCLxrtHmVUb2mcUbCHRfrLBkhI+JOByhp5AhTwJuveBh
Z9T4QocPCvfJBG0qqS/vQqXf3aNT25gegfmacnta3k8+f6JYoOIXrWcCAwEAAaOC
ASkwggElMA4GA1UdDwEB/wQEAwIBBjASBgNVHRMBAf8ECDAGAQH/AgEAMB0GA1Ud
DgQWBBT1zdU8CFD5ak86t5faVoPmadJo9zAfBgNVHSMEGDAWgBSP8Et/qC5FJK5N
UPpjmove4t0bvDA+BggrBgEFBQcBAQQyMDAwLgYIKwYBBQUHMAGGImh0dHA6Ly9v
Y3NwMi5nbG9iYWxzaWduLmNvbS9yb290cjMwNgYDVR0fBC8wLTAroCmgJ4YlaHR0
cDovL2NybC5nbG9iYWxzaWduLmNvbS9yb290LXIzLmNybDBHBgNVHSAEQDA+MDwG
BFUdIAAwNDAyBggrBgEFBQcCARYmaHR0cHM6Ly93d3cuZ2xvYmFsc2lnbi5jb20v
cmVwb3NpdG9yeS8wDQYJKoZIhvcNAQELBQADggEBAFsnfA30jsQHf3U8XxeJUHhV
EpESFSNyt7yf/zboXTvy7RG7hgFugyWfcS4WIhHIy9yYoTfSuFCj73Clc6x62EP7
5ros/YN38Q7zjaJKdSdJJ5+9Kq4fFQ5itED807y5maAzrMG4indOACzP9swinQ7C
daRO4z00bN2CKgJd4S0wQ6hQYqodPYLoRVZI2yqAxNGBI0DozuwiIQpYLPMk/Rza
vArdFMtyyKsWVCgQnRBCIS7AXUHHQcCasd5fg3WhZSLJRInEXALy4k5bGxjtNeby
CV/akHyNQxN+Lw3E4hxAT4wK0emK+UOQP3RbzWnljGbrVy56GKcQupSlAkclrDo=
-----END CERTIFICATE-----AlphaSSL Root CA certificate
-----BEGIN CERTIFICATE-----
MIIDdTCCAl2gAwIBAgILBAAAAAABFUtaw5QwDQYJKoZIhvcNAQEFBQAwVzELMAkG
A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv
b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw05ODA5MDExMjAw
MDBaFw0yODAxMjgxMjAwMDBaMFcxCzAJBgNVBAYTAkJFMRkwFwYDVQQKExBHbG9i
YWxTaWduIG52LXNhMRAwDgYDVQQLEwdSb290IENBMRswGQYDVQQDExJHbG9iYWxT
aWduIFJvb3QgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDaDuaZ
jc6j40+Kfvvxi4Mla+pIH/EqsLmVEQS98GPR4mdmzxzdzxtIK+6NiY6arymAZavp
xy0Sy6scTHAHoT0KMM0VjU/43dSMUBUc71DuxC73/OlS8pF94G3VNTCOXkNz8kHp
1Wrjsok6Vjk4bwY8iGlbKk3Fp1S4bInMm/k8yuX9ifUSPJJ4ltbcdG6TRGHRjcdG
snUOhugZitVtbNV4FpWi6cgKOOvyJBNPc1STE4U6G7weNLWLBYy5d4ux2x8gkasJ
U26Qzns3dLlwR5EiUWMWea6xrkEmCMgZK9FGqkjWZCrXgzT/LCrBbBlDSgeF59N8
9iFo7+ryUp9/k5DPAgMBAAGjQjBAMA4GA1UdDwEB/wQEAwIBBjAPBgNVHRMBAf8E
BTADAQH/MB0GA1UdDgQWBBRge2YaRQ2XyolQL30EzTSo//z9SzANBgkqhkiG9w0B
AQUFAAOCAQEA1nPnfE920I2/7LqivjTFKDK1fPxsnCwrvQmeU79rXqoRSLblCKOz
yj1hTdNGCbM+w6DjY1Ub8rrvrTnhQ7k4o+YviiY776BQVvnGCv04zcQLcFGUl5gE
38NflNUVyRRBnMRddWQVDf9VMOyGj/8N7yy5Y0b2qvzfvGn9LhJIZJrglfCm7ymP
AbEVtQwdpf5pLGkkeB6zpxxxYu7KyJesF12KwvhHhm4qxFYxldBniYUr+WymXUad
DKqC5JlR3XC321Y9YeRq4VzW9v493kHMB65jUr9TU/Qr6cf9tveCX4XSQRjbgbME
HMUfpIBvFSDJ3gyICh3WZlXi/EjJKSZp4A==
-----END CERTIFICATE-----After a fullchain.pem was created, I need to rename the privkey.txt to privkey.pem.
mv privkey.txt privkey.pemAnd lastly, open your vhost NGINX config file whether in your conf.d folder (/etc/nginx/conf.d) or sites-enabled (/etc/nginx/sites-enabled) folder.
Change both lines to:
ssl_certificate /etc/nginx/ssl/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/privkey.pem;
NGINX full config
Here's the nginx virtualhost full config:
server {
server_name mywebsite.com;
root /var/www/mywebsite;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html index.php;
location / {
# First attempt to serve request as file, then
# as directory, then fall back to displaying a 404.
try_files $uri $uri/ =404;
}
# This is for php handler, if you don't using php
# or using different lines, please don't copy
location ~ [^/]\.php(/|$) {
fastcgi_split_path_info ^(.+\.php)(/.+)$;
fastcgi_pass unix:/var/run/php/php7.4-fpm.sock;
fastcgi_index index.php;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_read_timeout 180;
include fastcgi_params;
}
# deny access to .htaccess files, if Apache's document root
# concurs with nginx's one
#
location ~ /\.ht {
deny all;
}
listen 443 ssl;
ssl_certificate /etc/nginx/ssl/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/privkey.pem;
ssl_session_cache shared:le_nginx_SSL:10m;
ssl_session_timeout 1440m;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers off;
ssl_ciphers "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384";
}
server {
if ($host = mywebsite.com) {
return 301 https://$host$request_uri;
}
listen 80;
server_name mywebsite.com;
return 404; # managed by Certbot
}
Replace mywebsite.com with your site, and don't forget to check your nginx config first with:
nginx -tand reload or restart nginx with:
systemctl reload nginxsystemctl restart nginxDone!
Little note
If you have other subdomains like shop.mywebsite.com and blog.mywebsite.com, you can copy the nginx config above, but make sure to replace every mywebsite.com with your subdomain! then reload nginx
Source for AlphaSSL intermediate and root ca cert: https://www.ssl2buy.com/wiki/alphassl-intermediate-root-ca-certificates
Thanks for reading.