If you already have an online windows server, your system may be attacked by a bot login into your system using brute force because the Windows Server uses the default port (port 3389) to access with Remote Desktop Connection application.
Windows Server logged those events on Event Viewer. You can check what kind of events by:
#1. Opening Event Viewer Application
First, you can open an "Event Viewer" application on your windows server.
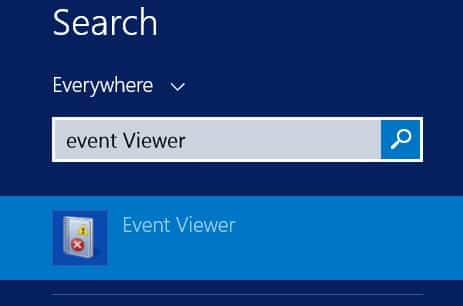
After the Event Viewer application was opened, open the menu Custom Views -> Server Roles -> Remote Desktop Services.
#2. Check Information events
There are 2 kinds of events on the screen. Information and Error events.
For example, Information Events contains IP Addresses that are trying to login into our system.
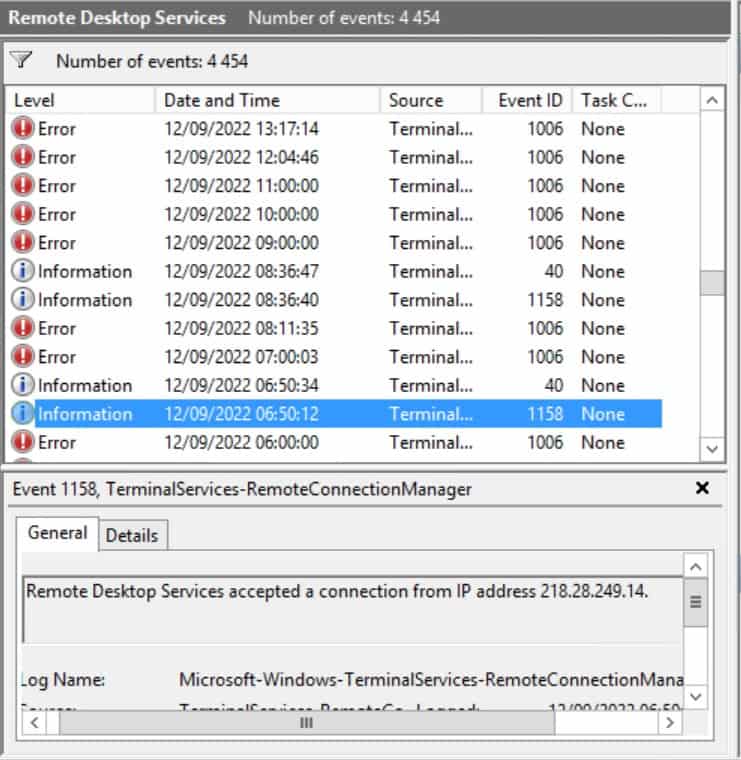
In the image above, on 12 September 2022 at 06:50:12, there is an information event with details: "Remote Desktop Services accepted a connection from IP address 218.28.249.14"
The IP address 218.28.249.14 is trying to connect to my windows server using the RDP port, which they are using a brute-force attack to logged-in to my server.
And that information event is followed by another information event on the same day 20 seconds later with details "Session 2 has been disconnected, reason code 0"
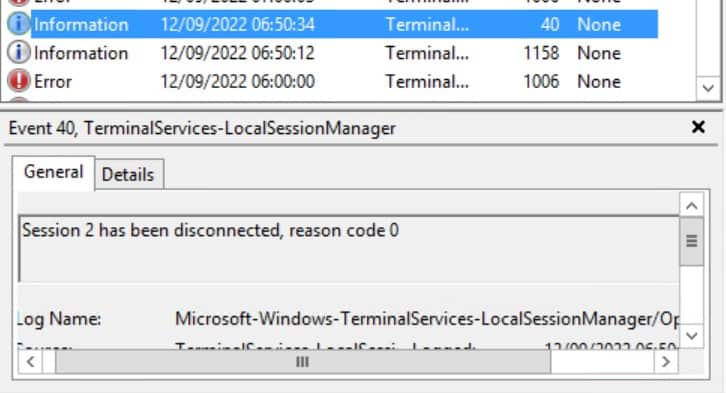
Their bot was unable to logged-in into my system.
This can happen every minute, every hour, every day, or maybe 24x7.
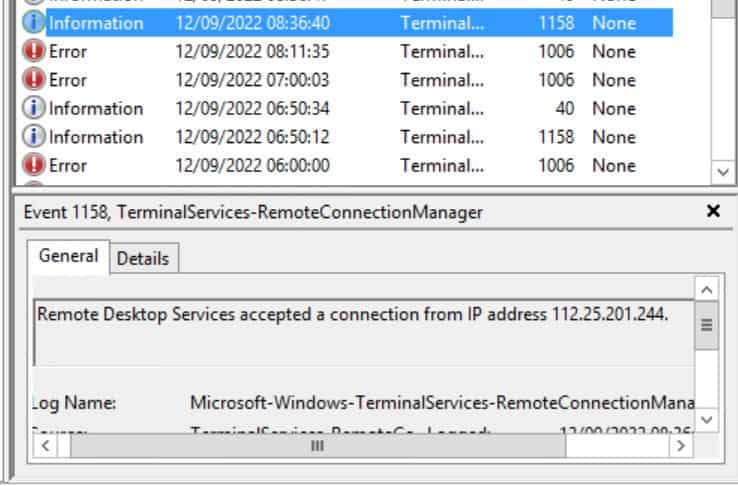
Another IP Address (Remote Desktop Services accepted a connection from IP address 112.25.201.244.) tried to logged-in to my system again.
Both IP Addresses are flagged as spam, you can check real-time IP Abuse Reports on websites like AbuseIPDB.com (IP 218.28.249.14, IP 112.25.201.244).
#3. Check error events
Windows Server logged error events for Remote Desktop Services (Server Roles) too on Event Viewer.
All error events details with a caption.
The RD Session Host server received large number of incomplete connections. The system may be under attack.
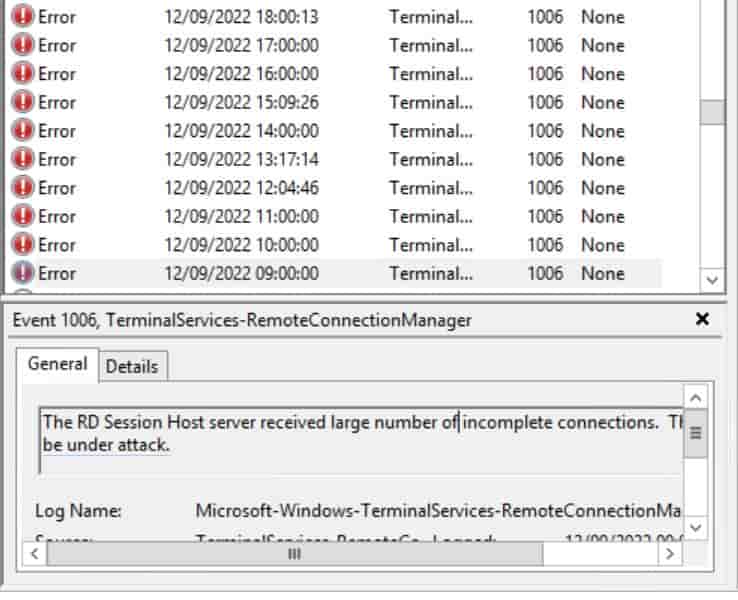
and it happens many times.
So, how do we prevent this? let's take a look at my other post: "How to allow only specific IP Addresses to access Remote Dekstop Connection on Windows Firewall" 😏
Thanks for reading.